Linux Desktop 2fa with Pam u2f
25 | 10 Jun 2015
Overview of Desktop 2fa and Passwordless Authentication
Two factor authentication (2fa) can improve security on laptop devices, by providing a 2nd layer of security to the authentication. Both security key and password are required to login.
Passwordless (token) Authentication helps improve security by reducing the number of times you need to enter your password whilst using the laptop. The less times you enter your password, the less oportunity for someone to capture it. Handy for on the train or in an internet cafe.
Implications of 2fa on Desktop
Pam u2f 2fa implementation depends on the integrity of your pam configuration files. Securing the pam configuration can only be achieved with full disk encryption. This prevents a thief from altering authentication configurations in the pam configuration. If you choose not to encypt your entire disk you can at least prevent the editing of your pam configuration from your own device by performing the following steps:
- Locking down the bios settings to prevent boot from network / usb / cd.
- Ensuring you have locked your grub config with a password preventing single user sign on or the boot of any rescue partitions.
With this setup the only way to alter the pam configuration would be to remove the drive from the laptop and attatch it to another computer where it could be mounted for editing.
Implications of Passwordless Authentication on Desktop
- lose of both your computer and your security token. The simple solution is to ensure your data is encrypted.
- Disk encryption becomes complicated, I've read articles looking into challenge responce implemementations with security keys and encyption protocols. These are promising but provide little security advantage if both your laptop and security token are lost.
- lose of token (Bakup security token in safe).
Task / Role Reccemendations
- login
- encryption wrapped by password
- security token (2fa)
- sudo
- Passwordless Authentication
- su
- Passwordless Authentication
Implemention Tasks
- configure a Yubikey
- build pam module
- u2f configuration
- pam configuration
Building the Pam Module
On debian or centos you will need to build hidapi, libu2f-host, libu2f-server and pam-u2f. hidapi enables communication with usb security keys, u2f-host implements host-side of the u2f protocol (communication between the key and the server), u2f-server provides the authentication to u2f-host, and pam-u2f is the pam module for the u2f-server.
Configure a Yubikey
If the key is a neo key you'll need to use neoman to ensure u2f is enabled. To get the system to register the key and be able to use the key as a non privelidged user first setup a new group, then add permission to this group for the key using a udev rule.
sudo groupadd u2fkey
sudo usermod -a -G u2fkey jack
sudo usermod -a -G u2fkey jill
lsusb | grep Yubi | cut -d " " -f 6 | awk 'BEGIN{FS=":"}{print "ATTRS{idVendor}==""$1"", ATTRS{idProduct}==""$2"", GROUP="u2fkey", MODE="0660""}' > /tmp/99-my-u2fkey.rules
# check the rule
cat /tmp/99-my-u2fkey.rules
sudo mv /tmp/99-my-u2fkey.rules /etc/udev/rules.d/
Hidapi-hidraw
apt-get/yum install git autoreconf
git clone https://github.com/signal11/hidapi
cd hidapi
autoreconf --install
./configure
make
make install
Centos 6.6 Note
If any of the configs fail, locate the required package config and export PKG_CONFIG_PATH prior to configuration. example;
locate hidapi-hidraw.pc
export PKG_CONFIG_PATH="$PKG_CONFIG_PATH:/lib64/pkgconfig:/usr/local/lib/pkgconfig"
libu2f-host
git clone https://github.com/Yubico/libu2f-host
cd libu2f-host
autoreconf --install
./configure
make
make install
libu2f-server
git clone https://github.com/Yubico/libu2f-server
cd libu2f-server
autoreconf --install
./configure
make
make install
pam-u2f
git clone https://github.com/Yubico/pam-u2f
cd pam-u2f
autoreconf --install
./configure
make
make install
u2f configuration
To stepup u2f on your system you'll need to configure a file containing keys for your u2f implemenation. One of the new tools installed is called "pamu2fcfg", use this to setup /etc/u2f_mappings.
pamu2fcfg -u bob > /tmp/u2f_mappings
# now touch the button on the yubikey
sudo mv /tmp/u2f_mappings /etc/u2f_mappings
Pam Configuration Options
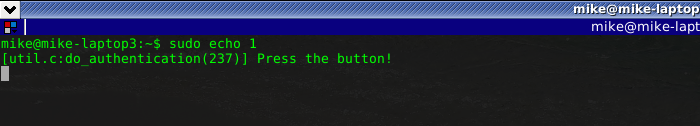
you can read about all the various options for the pam module on the githib page or in the README.md downloaded with the git checkout. I was so used to entering a password I ended up wondering why my computer was going slow and not asking me for a password, so i updated the code to add the cue option which simpley prompts you to push the button.
Pam Configuration Sudo
/etc/pam.d/sudo
# u2f authentication
auth sufficient pam_u2f.so authfile=/etc/u2f_mappings cue
Pam Configuration Su
/etc/pam.d/su
# u2f authentication
auth sufficient pam_u2f.so authfile=/etc/u2f_mappings cue
Pam Configuration Login
/etc/pam.d/login
# u2f authentication
auth required pam_u2f.so authfile=/etc/u2f_mappings
Pam Configuration Slim
/etc/pam.d/slim
# u2f authentication
auth required pam_u2f.so authfile=/etc/u2f_mappings
And that's it, whenever you loging or using sudo you'll either be using two factor authentication, or authenticating using only the security token.